GGvulnz aftermath - How I forced Google to redesign Groups*
I’m a bit late with this post, but people were wondering if the methods described in the first GGVulnz post are still applicable today.
I’m a bit late with this post, but people were wondering if the methods described in the first GGVulnz post are still applicable today.
In short, they are not.
Google has released a new design of Groups which solved the main problems that enabled the exploit with the registration emails.
The new Groups UI completely lacks the old “forumsearch” view, so you can no longer list the public groups / mailing lists of a public domain.
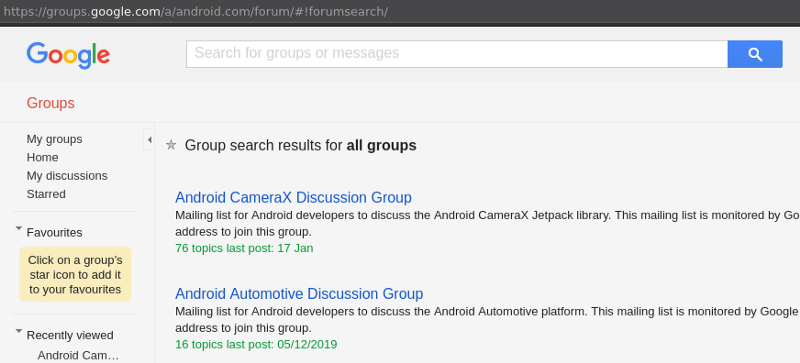 This view is gone
This view is gone
This page was also where you could search for emails even when there were no public lists. So searching in a public domain is gone as well.
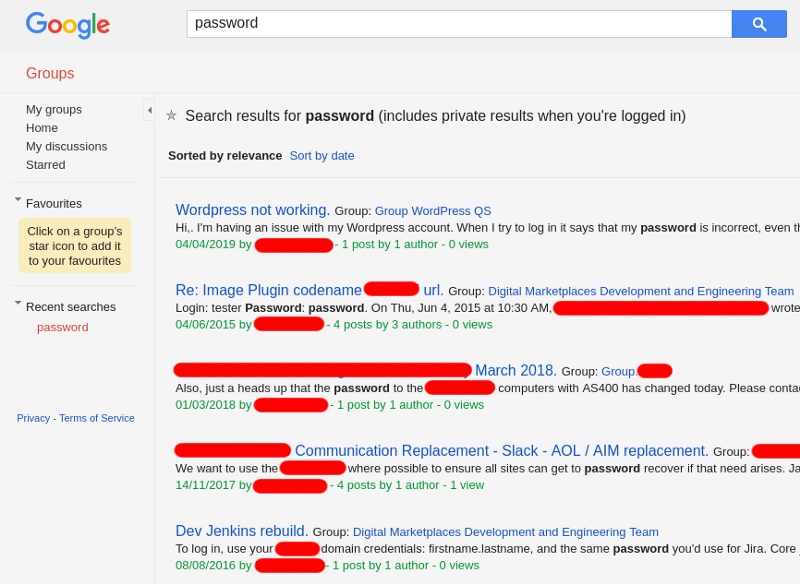 This is gone as well
This is gone as well
With these changes the original logic flaw is essentially rendered infeasible, since you can’t easily find vulnerable groups.
The exploit technically should still work but you would also have to guess the name of a public group within the domain.
Public groups can be accessed in this format:
https://groups.google.com/a/$domain/g/$listname
You can still check the necessary permissions in the About page of the new design:
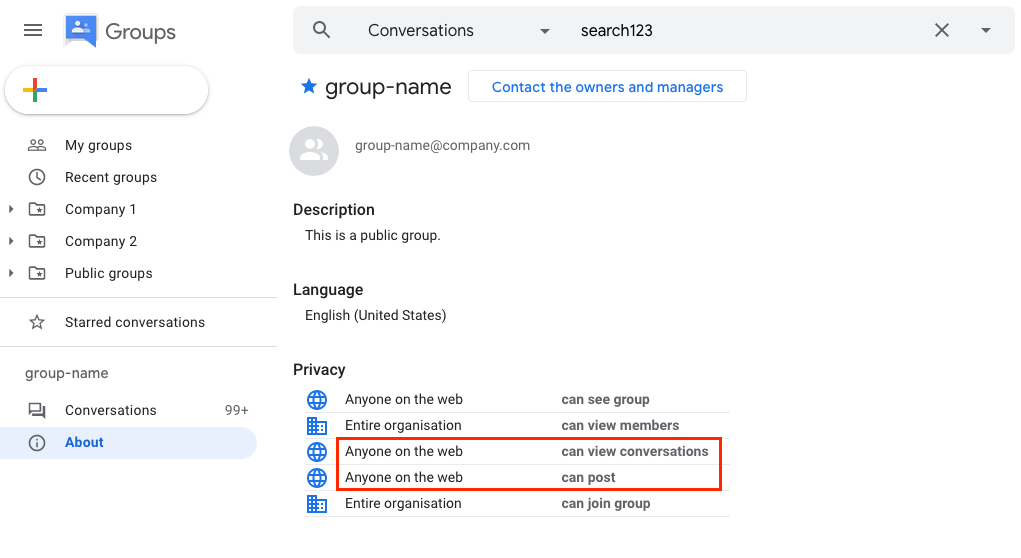
Timeline of the new design rollout:
March 9, 2020 - (less than 2 months after my blog post) - Beta launch
May 26, 2020 - New design is generally available
September 15, 2020 - New design is the default for all users
November 10, 2020 - Old design is turned off
September 17, 2020 - Updated interface for admins to control permissions. This might seem trivial, but having a clear UI for admins is a big step forward in preventing accidental misconfigurations.
*Of course I cannot possibly know whether my work has anything to do with the new Groups UI, since removing the “forumsearch” view is not shown under Deprecated features.
GGvulnz might not be the sole reason behind the new UI, but I think it was at least taken into account during design. You can’t just leave out a core feature - the list of public groups - accidentally. I guess the old design allowing the exploit wasn’t actually “Intended Behaviour” as Google claimed.
I ended my previous post with this: “I’m publishing this in the hope that the publicity would push Google to mitigate the risk and also to help raise awareness.” It appears that sometimes whining on the Internet actually works. Although I would’ve preferred if my original report was accepted.
I’m a bit late with this post, but people were wondering if the methods described in the first GGVulnz post are still applicable today.
This logic flaw is the lovechild of two previous reports: